Any of us could fall victim to cyberattacks – how to protect ourselves? Part 2
Last week, we provided you with an introduction to the dark world of cyberattacks. For this week’s article, we asked Trinidad Wiseman’s development team whether it matters which content management system you use in terms of security and who is responsible for security incidents. We also provide you with a list of recommendations to help you prevent cyberattacks against your website and computer system.
Which content management system is the most secure?
If we compare the most popular content management systems (CMS) used in Estonia, then Drupal is considered to be a little bit more secure than WordPress. You can also check out our earlier article about the newest version of the CMS, Drupal 9.
In both cases, problems usually arise when using third-party plugins. Often, these are created by a single developer who works on the plugin during their free time, which means that they usually do not have time to conduct security tests and will only get around to patching vulnerabilities after something has already gone wrong.
Which CMS to choose depends on what the platform will be used for – for example, bloggers will likely not need to worry about security as much as the owner of an online store who is responsible for things like customer data and money transfers.
We suggest that you first consider your needs and then evaluate whether a specific platform meets your requirements (e.g. do you wish to start a blog or to create a business-critical self-service platform).
If you want to ensure a good level of security, we recommend opting for a bigger and more popular CMS. This guarantees a high level of trust and a lot of feedback from the community, so if you come across any problems, you can ask for help via numerous forums and channels (e.g. a Slack channel, stackoverflow).
If you wish, you can also use smaller and lesser-known solutions or even build your own platform, but in that case, you must ensure that any vulnerabilities are patched. You can order various security audits and decide how often you want to have one done.
In our experience, the biggest problem is a lone client who has to work alone to ensure that no vulnerabilities exist. Since content management systems are very easy to set up nowadays, then there are a lot of websites and online stores out there where the owners do not even know that they must update their security software every once in a while. Often, they do not even use HTTPS.

Who is responsible in the event of a security incident on my website?
Responsibility is determined by the origin of the problem, whether it is sloppy code written by the developer, security updates that have not been installed, carelessness on the server host’s end, or a mistake made by the admin (e.g. if they have installed third-party modules without talking to the developers first).
But frequently, the situation may be a lot more complicated than that, for example, if the website was created a long time ago with a third-party interface, but the service provider who used to provide the interface is no longer actively working on the service.
In such a case, the code will not have been updated in years and hackers will be able to exploit weaknesses in it. Who should be blamed or made responsible in such a case?
It is the duty of the developers to always recommend and offer the client the best security update solutions. If the client does not wish to or is unable to pay for this, then that unfortunately means an increased risk of a vulnerability appearing.
Most of the time, clients will be hard-pressed to make any one person responsible for security incidents. Instead, it helps to have preventive measures in place and, if necessary, to insure your website.
How to increase security and to protect your website against cyberattacks?
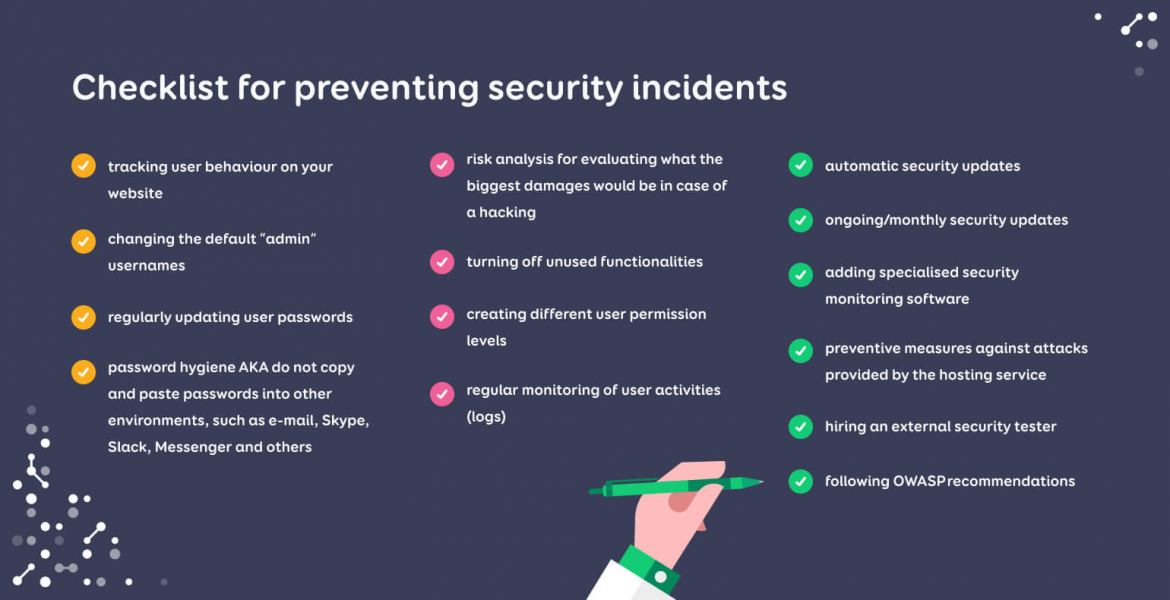
The most important thing is to do monthly security updates and to have various preventive measures in place, such as automated monitoring conducted by separate service providers that provide more security (e.g. GTMetrix, Pingdom, and also AppDynamics, whose licences we sell at Trinidad Wiseman).
For additional security, you can also install platform-specific plugins. But remember to mark down the last time they were updated and the number of active users on it.
Automatic monthly updates, such as the ones for Windows or your phone, may not be enough to guarantee the best results. Why?
Technology is evolving very rapidly today, which also means that cyber criminals are often a couple of steps ahead of us and are already identifying exploitable bugs that product and system owners are not even aware of yet.
Let us look at an example: we can view the core of the CMS and the plugins you have installed as completely separate parts of the system since the developers of both have no way of accounting for how your website has been developed.
Due to this, the developers of different, individual parts may make changes to their product that no longer matches the rest of your website’s code base and some functionalities may stop working after you install the update.
This is why it is very important to also have your developers manually monitoring your website. If your website is big, then we recommend hiring a maintenance partner who can check all the functionalities on your website after you install updates. If necessary, they can also restore previous functionalities in the updated code.
How to prevent cyberattacks from the get-go?
Ensuring security takes time and resources. Often, people will first get a painful lesson and only then start paying attention to security. But how to prevent this from happening in the first place?
"In the online world, there is a constant struggle between convenience, cost, and security, and everyone must find a suitable balance for themselves between these. You should start with how people behave online."
The biggest mistake people make today is with their passwords. Usually, they use something simple and easy to remember, and they will use that same password everywhere.
Check if your passwords are among the most common passwords of last year or whether you can find your e-mail address among those that have been leaked after a data breach.
If so, then your password has leaked, and we recommend that you change it as soon as possible and that you use different passwords on different platforms. Why is this important?
If your password should somehow get leaked, then if you use the same e-mail and password combination everywhere, it can be easily used to hack into all of your accounts, which can then be used for ill purposes.
Systems will sometimes force you to update your password. However, if it does not save your old passwords and does not check those against the new password, then the user will usually use a password similar to their old one out of convenience – for example, they may only change two numbers in it –, which makes their new password very easy to guess.
To save your passwords, use a convenient and secure password manager that you can use on a computer, an iPhone, and an Android phone. We recommend LastPass, Keeper, BitWarden, 1Password.
You can read reviews to help you make a decision on which one to use. It is not a good idea to save your passwords to a notes app – if you use an iPhone and an unauthorised person gains access to your iCloud account, then they will also gain access to your notes and thus, your passwords.
Before opening a link to any website, whether it is in an e-mail or elsewhere, you should thoroughly examine what kind of link it appears to be and whether you should actually click on it.
To better protect your website, we recommend turning off all functionalities that you are not using. If your website is meant to be informative and requires no actions to be taken by the visitor, then turn off commenting and signing up.
If you discover a non-existent user, then we recommend restricting that user’s access based on their IP address and then checking all of their activities on your website (logs).
It is important to regularly check and scan all activities on your website. To do this, you must make sure that all activities leave behind a trace (e.g. who logged in and when, which user changed something somewhere etc).
It is a good idea to limit the permissions given to users by their account level and to regularly double check all active users and the permission levels given to different users. Quite often, there is an account that has been given the highest permission level after its creation, but is then cast aside and never used.
Often, companies forget to deactivate the accounts of employees who have left their jobs. This should be written down as a separate task in the company policies and procedures.
How to choose a plugin? The latest release of the module should usually date back half a year or up to a year max and ideally, it should have at least 100 000+ users in the case of WordPress (Drupal may have less). It is also important to read user reviews (are there a lot of issues, how quickly does the developer respond etc).
Here is a checklist based on the preventive measures mentioned above to be used as a quick reference.