Resolving security challenges, a case study: the development of SK ID Solutions’ e-service portal
Many of us are likely very familiar with Smart-ID, Mobile-ID and the ID-card authentication methods. Maybe you have even felt that in Estonia as well as the Baltics as a whole, there are less and less people who do not use Smart-ID or Mobile-ID services every day. This is largely the result of the work done by SK ID Solutions for over 20 years.
SK’s goal is to create products and services that allow both the public and private sector to authenticate users securely, sign documents, and legally e-stamp official documents for long-term storage.
Their solutions are the cornerstone of e-Estonia and today, more than 4 million people in over 20 countries across the world use just the authorisation and certification services provided by SK ID Solutions.
About the project
In cooperation with SK, we started creating an e-service portal that would allow clients to create new orders and manage pre-existing ones. Since there are a lot of requirements set for security services and it is generally not enough to just place an order, then we also set ourselves the goal of optimising the daily tasks performed by SK’s in-house specialists.
The foundations of the project became security, usability, automation, and dynamic expansion. As a result of this cooperation, the SK e-service portal was born, allowing users to get acquainted with the options available to them even more easily and to choose a product or service suitable to their particular needs straight in the portal.
The work processes of specialists have been made more streamlined and daily tasks are now based on much more integrated automations.
A selection of challenges:
- unlike with classic self-service solutions, the products offered by the SK e-service portal are very complex by nature;
- the products have a lot of intertwined correlations, rules, and limits that all need to be taken into account;
- security is not just a slogan, but a structural philosophy;
- a large number of validation rules made migrating data from the earlier system more difficult.
If you're looking for a solution tailored to your business needs, explore our software development services on our website and get in touch with us.
How did we resolve these challenges?
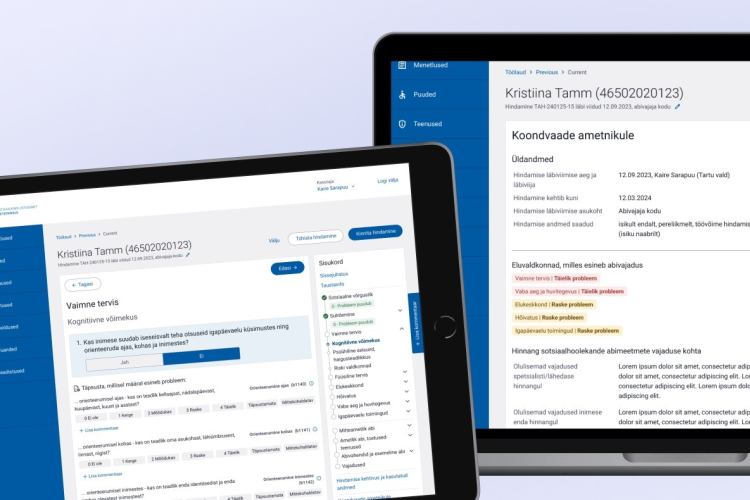
The SK e-service portal is the union of an online store’s self-service platform and an order management system. The ordering process must be as simple as possible for the end user. It must be said that unlike classic products that we usually order from online stores (such as clothes, electronics, food), ordering cryptographic certificates and identification services is much more complex.
Here is a breakdown of how we resolved the 7 biggest challenges in this project.
1. Understanding the knowledge profile of the users: the products are not easy to comprehend by their nature, which made it crucial to have a detailed understanding of the users’ knowledge profiles. The clients being serviced include users from both the private and public sectors as well as a variety of areas. The terminology, which may be familiar to specialists from the ICT sector, is oftentimes uncomprehensible to non-technical clients.
2. Providing a detailed description of the products: although you can always turn to SK’s managers with any questions you may have when placing an order or simply scour the internet for answers, we saw the value of providing a detailed description of the products during our discovery phase of the project. As a result, we wrote out thorough descriptions for each product that bring out the nature of the product as well as its potential use cases.
3. Analysing the connections between products: concerning the products and services, we paid extra attention to the connections between them that affect the ordering and management processes. Unlike when ordering a pair of shoes, where there are no procedural conflicts when ordering an identical pair, SK’s products are connected to companies through a so-called unique handshake that must not have an existing duplicate.
4. Fulfilling special requirements: it is also important to acknowledge the special requirements that apply to different products and that are impossible or impractical to fulfil without the associated products. To prevent potentially failing orders from being placed and the frustration that would create, we made sure to pay careful attention to the numerous validation rules and associations during the design, analysis, and development phases of the project.
5. Ensuring security: the cornerstone of all of SK’s products and services is security. It is not possible to provide an e-stamp service that is comparable to a notarised signature without having trust in the service being offered. Additionally, the team must have a sharp eye and be very precise to gather, handle, and store large amounts of sensitive data. In such a context, security does not simply mean having superficial rules, but a whole architectural foundation that provides efficient support to the development of the application.
To ensure security, it is important to have a clear overview of who did what, where, and when. It is also important to follow the principles of data segregation and the capabilities and construction of the hosting server that supports the application. To avoid any potential weaknesses, we covered a huge part of the code repository with automated tests. A cyber security expert audited the e-service portal’s final version’s compliance with various rules.
6. Focusing on the whole when migrating data: in essence, the e-service environment already existed prior to the analysis and development of the new version. This meant that although we had created a new and better e-service portal that incorporated additional requirements and rulesets, the new solution could not work before data was fully migrated from the old one. Data migration is often a complicated process because the new architecture, database, and ruleset do not have backwards compatibility with the previous solution or its work processes. This creates conflicts between datasets which must be resolved for the new solution to work cohesively.
7. Iterative migration: from the very start of the migration process, we realised that we would have to take an iterative approach towards handling the information concerning the users, orders and additional data associated with those orders for thousands of companies. It is impossible to perfectly copy over hundreds of thousands of entries in one go and unreasonable to go through the database manually. By taking a procedural approach, the conflicts made themselves known, which made it much easier to migrate the whole.
Conclusion
Together with SK ID Solutions, we set ourselves the goal of creating a new, more functional and user-friendly e-service environment. By servicing both in-house and outside users, we started resolving many challenges connected to both security as well as the complex nature of the products.
At Trinidad Wiseman, we use an agile and methodical development process, which was how we created the SK e-service portal that allows both new and existing clients to choose and manage services in a much more straightforward manner. You can find more information about our development process here.