Security practices in Atlassian Cloud
NB! Please note that Atlassian products are developed rapidly. The product features listed in the article may change over time.
Cloud product security relies on Atlassian’s internal environments
Atlassian practices a layered approach to secure their networks. Controls are implemented at each layer of their cloud environments, dividing infrastructure by zones, environments, and services.
Environments are separated to limit connectivity between production and non-production environments, and production data is not replicated outside of production environments.
Services are explicitly authorized to communicate with other services through an authentication allowlist.
Access to sensitive networks is controlled through the use of virtual private cloud (VPC) routing, firewall rules, and software defined networking, with all connections into those networks encrypted.
Certificates and Atlassian Trust Management System
Atlassian has acquired many security compliance certificates: PCI DSS, SOC, ISO/IEC 27018, ISO/IEC 27001, VPAT, FedRAMP.
Based on the ISO27001 Information Security Management System standard, Atlassian Trust Management System (ATMS) explains how concepts of different certificates are implemented into security practices.
The basis of the ATMS is a strategy that covers best practices from both the ISO27001 standard as well as the Cloud Security Alliance (CSA) Cloud Controls Matrix (CCM).
In order to continuously evaluate potential risks to Atlassian’s environments and products, the company is performing on-going risk assessments based on ISO27005 or ISO31010 Risk Management methodologies.
In many cases, especially in the case of their products, these are performed as technical risk assessments or code reviews. However, Atlassian also evaluates each of their entire product stack or a portion of organization to uncover higher level business risks.
A structured Trust Management Forum includes representatives from every pillars of Atlassian’s Trust program to ensure they apply not only security controls but also reliability, privacy and compliance controls and how to manage risks across each of these pillars.
Configuring product security - how to minimize possible risks yourself?
In essence, Atlassian Cloud security policies are build on Zero Trust concept.
Zero Trust is a framework in which an organization forgoes one large perimeter in favor of protection at every endpoint and for every user and/or device within a company.
Every tools acts as an independent unit that does not grant access to next tool.
You can implement identity authentication mechanisms (such as SSO, SCIM, and 2-factor authentication) across your Atlassian Cloud products with Atlassian Access.
Devices on different service access tiers can be authenticated according to its certificate with Duo.
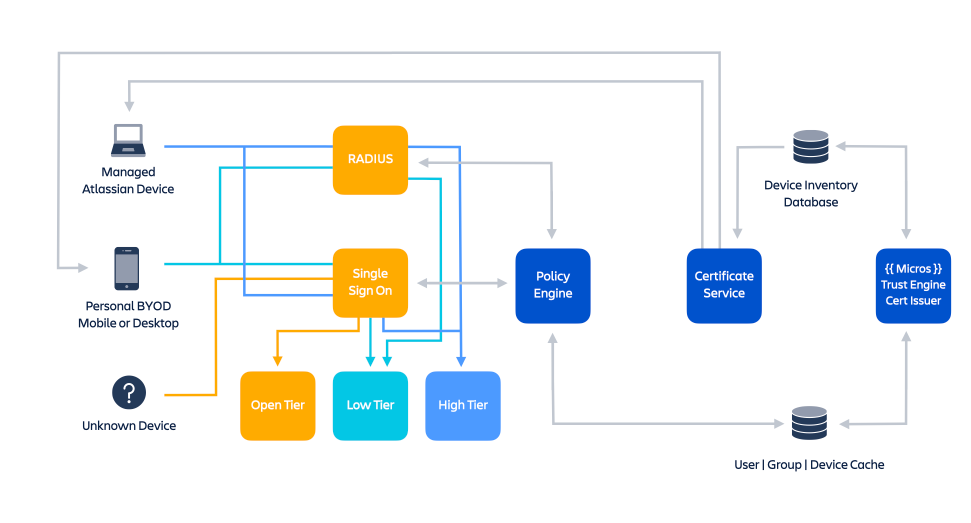
User and device authentication logic implemented in Atlassian.
Atlassian assumes responsibility for security, availability and performance of the applications they provide, the systems they run on, and the environments within which those systems are hosted.
However, security is a joint responsibility between Atlassian and customers.
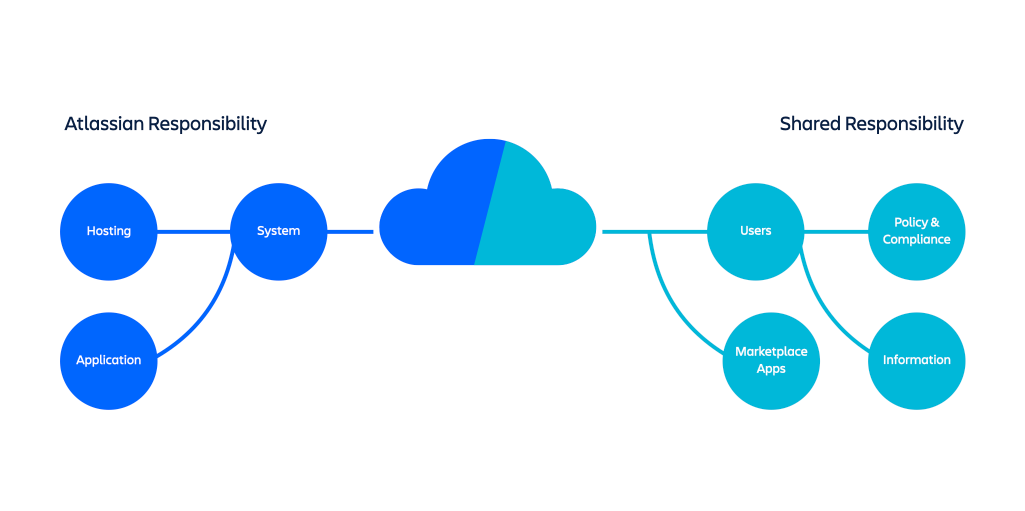
Responsibility distribution across Atlassian Cloud products.
Built in and optional security features in Atlassian Cloud products
- data encryption - encryption in transit and at rest. Included in every Cloud plan (Jira Software, Jira Service Management, Confluence);
- backups - automated daily backups that are retained for 30 days. Included in every Cloud plan;
- data residency - data residency for United States and European Union. Available on Standard, Premium and Enterprise plans;
- audit logging - organization-level audit logging available via Atlassian Access (Jira Software, Confluence), product-level audit logs (Jira Software, Confluence);
- device security - mobile device management support (Jira Software, Confluence, Jira Service Management);
- content security - IP whitelisting for Premium and Enterprise (Jira Software, Jira Service Management, Confluence) and web session duration management;
- API and app security - API token controls (Jira Software, Jira Service Management, Confluence).
Atlassian Marketplace security programs
Atlassian implements several programs and frameworks to minimize risks regarding plugins:
Marketplace bug bounty program
The program aims to give partners the tools to facilitate post-production vulnerability discovery in a cost-efficient way. If you are looking to start or extend your security story.
Security self assessment program
The program involves an annual security self-assessment that Atlassian reviews and approves. During the review process, Atlassian works with the partner to pinpoint vulnerabilities and identify improvements.
Vulnerability disclosure program
The Vulnerability Disclosure Program(VDP) for all third party Marketplace cloud apps provides a framework for Atlassian to securely accept and triage vulnerabilities submitted by Atlassian customers and security researchers, and then report those vulnerabilities to partners to remediate.
Ecoscanner
The Ecoscanner platform is a platform used for performing security checks against all Marketplace cloud apps on an ongoing basis.
Security bug fix policy
The policy describes how and when Atlassian expects their Atlassian Marketplace partners to resolve security bugs in their apps listed in the Marketplace.
Cloud Fortified apps program
Cloud Fortified Apps is the program for a new designation of apps designed to serve largest customers and those with more business-critical operating requirements when it comes to apps:
- security program participation: Marketplace Security Bug Bounty Program and Security Self-Assessment Program;
- reliability program participation: core capability SLOs + tests, and incident management;
- support program participation: provide a support point of contact, and respond to T1 support tickets within 1 day (24 hours).
If you need help implementing Atlassian Cloud
Do not hesitate to contact us – we provide consultations and can help with everything regarding Atlassian products and plugins.